One of the most desirable features of cryptocurrency is its anonymity and the fact that it’s decentralized. If your cryptocurrency is in a cold storage wallet no central authority can charge a late fee, put a hold on your funds or report your accounts to a government agency. You will need to become knowledgeable about digital security and common scams to protect your cryptocurrency investment.
If you send funds to the wrong wallet there is no bank to reverse the transaction. If you lose your passwords and seed phrases there is no one in control to bypass the security. If someone scams you it is your responsibility and most likely your investment is gone forever.
What you actually own is cryptographic keys that give you access to a wallet that can access information on the blockchain. Your wallet, your responsibility.
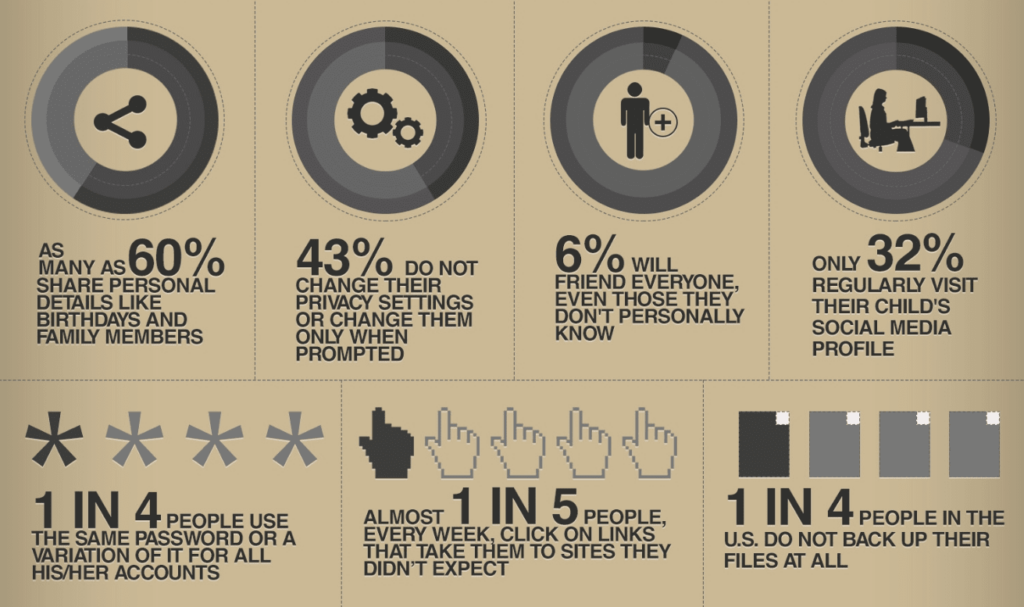
Finance applications have a history of being compromised and banks interfering in the finances of their customers is a daily occurrence. If you believe that you can adhere to basic security protocols then your assets are better off in your own hands.
Here are some tips to keep from getting scammed or having your Bitcoin and other cryptocurrencies stolen.
Make Digital Security a Priority
The first line of defense against hackers is the security on your personal computer and other devices. An ounce of prevention is worth a pound of cure. You cannot protect your cryptocurrency if your security pyramid is built on loose sand.
Do Not Visit Sketchy Sites
The average person can reduce the risk of encountering malware by over 90% simply by not opening attachments and avoiding websites with questionable security practices. This includes all pornography websites, websites without an SSL certificate, and websites that use antique programming.
Most anti-virus programs have an online component built in these days. If you have any doubt that a website is legitimately safe then use an online scanning tool like siteguarding.com to check for security issues. Site guarding checks the website against over 100 security and spam blacklists.
Invest in a Quality Anti Virus Software
If you can afford a computer or smart phone then you can afford anti-virus protection. The cost of a single intrusion can be substantial. If you invest in crypto then the stakes are that much higher.
Norton, McAfee, Kaspersky, Bit Defender and Web Root are all reputable options. It doesn’t matter as much which one you choose as it does that you pick one.
Password Management
You should use different passwords for different accounts. Your bank account shouldn’t have the same password as your email and your email should not have the same password as your social media.
Since most account passwords can be reset through your primary email, this is one of the most important passwords to protect along with any account that allows direct access to your finances (exchanges, online banking, crypto wallets, etc.).
- Change your passwords regularly. At least once every 3-6 months.
- Don’t use any information that can be found online such as birthdates or pet names
- Never send your passwords in an email or write them in a document on your computer.
Use password managers to generate stronger passwords. Use 2FA (2-factor authentication) when available. As with everything you should investigate these applications to be sure they aren’t another scam used to gain account access.
Tips for Generating Strong Passwords
- A password should contain at least 15 characters.
- The password should contain a mix of these 4 types of characters: upper-case letters, lower-case letters, numbers, and special characters..
- Avoid common names, slang words or any words in the dictionary. Brute force attacks will use word lists to speed up their attack.
- Don’t include any part of your name, the website the password is for, or other common information that could be found online.
- Choose an especially strong password for websites that hold your most important personal information. Social networks, email, and banks should all be considered highly sensitive.
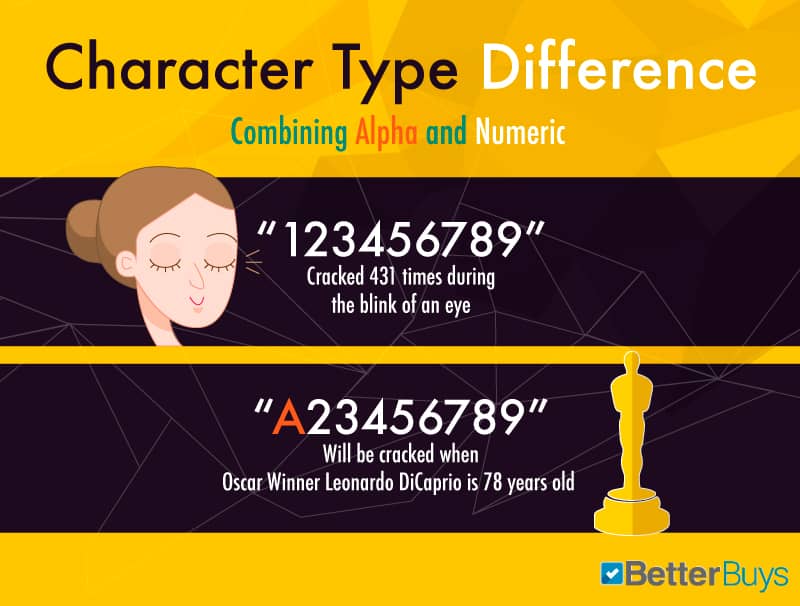
Each additional character makes cracking a password exponentially harder. For instance a 9 character alphanumeric password will take 3 months for an average desktop computer to crack but a 10 character password would take over a decade. An 11 character password would take more than 360 years!
When creating a password consider that governments and hackers have computers capable of operating several thousand times faster than desktop computers. Consider that the number of transistors on a microchip doubles about every 2 years. A 9 character password took 4 years to crack in 2000 but would only take 3 months to crack in 2016.
You are creating passwords to protect against future attacks, not one today.
Should You Write Your Passwords Down?
Contrary to what you may have been told, it is ok to write down your passwords as long as your store them securely. There is a 1 in 4 chance that your current computer will be infected with malware. The odds of having your home burglarized is roughly 1 in 200, or 0.05%.
Considering the burglar would then need to identify what the paper was referring to, you’re much better off using a complex password and writing it down than using a simple password.
Use Multiple Email Addresses
You can add an extra level of security simply by using a separate email address for shopping and signing up for websites. If you plan on adding a lot of assets to an account you may even want to use a unique email address that is only used once.
Gmail and Microsoft Office 365 let you use “plus” email addresses for this purpose. So John Smith can sign up for Amazon with “[email protected]” and sign up for Facebook with “[email protected]”, but messages sent to each address will land in the inbox of [email protected].
A hacker would recognize this trick but most hackers will use scripts to speed up their work. Your compound email address may be enough to prevent an identity theft some day.
Monitor Data Breaches
Even large tech companies that are household names have been the target of hackers in the past decade. Yahoo, LinkedIn, Myspace, Mashable and many more have suffered from data breaches that allowed hackers access to all types of user data. In some cases they retrieved the emails, usernames and passwords of all users.
This data is sold on the black market and eventually ends up publicly available on the dark web or added to combo lists.
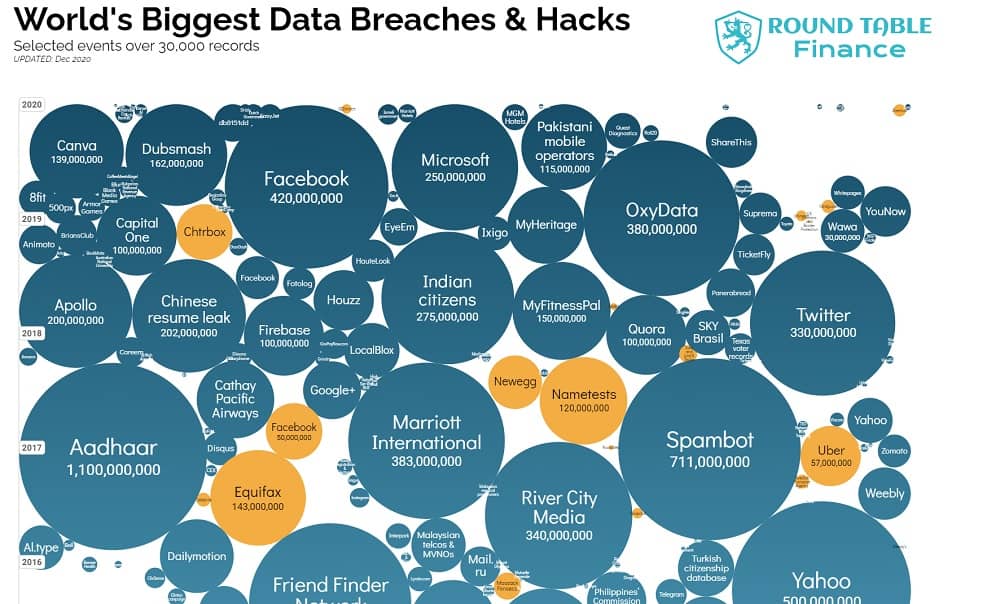
When hackers target you they will pull up a combo list and try all your existing passwords on your accounts to try and gain access. All it takes is reusing a compromised password once to have your identity stolen or have your bank account drained.
Credit Karma offers free security breach monitoring for users. It actually identifies passwords that have been included in known data breaches so you can address those quickly. Another great tool is the Have I Been Pwned Website which allows you to check your emails for security breaches in real time.
Your data may already be out there. There is just so much available that you may not find out until you are targeted by a hacker that checks.
Keep a Low Profile
When I took the role as Marketing Lead for the TWA Adventure Fund I was alerted to several hacking attempts originating from the middle east within 48 hours.
The hackers assumed that I would have access to lots of tokens and they quickly tracked down several of my social media accounts and cross referenced my logins and emails with combo lists.
Unfortunately I had been using the same password on one of my accounts for nearly a decade. Luckily the network identified the login as unusual and locked my account down while I was notified.
In my line of work it isn’t always possible to keep a low profile, but you should never draw more attention to yourself than you have to.
Never brag about how much crypto you hold. This is like an old man flashing hundred dollar bills when he pays for gas or dinner – you never know who is watching and who will be waiting in an alley when he leaves.
Scrutinize Applications You Use
Now that you have your basic online security taken care of you will need to make sure that you do not hand over the keys to the kingdom. You can’t protect your cryptocurrency if you are tricked into handing over access directly to a scammer.
Scammers will build replicas and competitors for every product and company out there. It’s not difficult to identify a website that is posing as another, but it can be tricky to tell whether a new application that promises enticing rewards is an honest business or a scam in disguise.
DeFi (decentralized finance) surged in 2020. Hundreds of apps and lending services popped up, most of them working in conjunction with the popular cold storage wallets that offer API access.
For example Uniswap works by connecting Metamask, Trust Wallet or another cold storage wallet to their exchange, completing your trades and then revoking access.
I don’t mean to make you fearful. Metamask is a secure application that is generally safe to use with web based applications. The risk comes when people start using new browsers that target crypto users like Cryptotab. A browser is capable of reporting tons of data back to its network. This is why Metamask has added features like blocking screenshots on the app.
You’re not only protecting your assets from a nefarious developer, but also from applications that may not have security and operating procedures that are sophisticated enough to stop third parties from hacking them. Any cryptocurrency related company should put security in the forefront of their marketing.
How Can You Tell?
To be safe an application should at first have an open public profile. If everyone knows everything about a company’s CEO and employees they are less likely to participate in a scam because they would have to go into hiding from angry victims.
Company officers should have a good track record. If they have a reputation for being ethical then you can expect that they will remain ethical. If they were capable of managing security for other projects then they are much better prepared for managing security on this one.
One of the major advantages of crypto is that the community crowdsources security. Companies will publish their code to github for others to analyze. All potential investors come together and scrutinize the staff, product, coding and prospects in communities all across the Internet. You can protect your cryptocurrency easier when you leverage the experience of others.
Join a Reputable Community For 2nd Opinions
One of the most powerful tools for protecting your cryptocurrency is the community you surround yourself with. Your connections will be a source for good ideas and a way to help identify bad ones.
If you’re about to make a mistake there is almost always someone that has already made that mistake before. Also a good community will have members that are specialized in identifying frauds. The best teacher is experience and it is an unfair advantage for new investors to crowdsource experience; an unfair advantage you must use.
There are active cryptocurrency communities on Reddit, Facebook, forums, and especially Telegram. Round Table Finance operates communities on Facebook and Telegram.
I also recommend the Crypto World Adventure group which is run by my friend Adrian Woodward. He has been investing in crypto for a decade and has experience with Bitcoin and DeFi.
Learn to Identify Different Types of Scams
It takes someone with a high level of skill to develop an application to steal your passwords, but anyone with average intelligence can engineer a convincing scam. Over $44 Billion was lost to online scams in 2019 alone.
Since cryptocurrency attracts many new investors and is decentralized by nature it has become a haven for scammers.
If something sounds too good to be true, it probably is.
Phishing Scams
Phishing is the fraudulent practice of sending communications purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers. Phishing scams will often include a fake website or in the case of Crypto a fake token.
It is your duty as an investor to check the authenticity of all communications, applications and tokens.
Since many projects are new scammers can get up on fake websites, fake coin gecko listings, and fake tokens quick enough that even Google believes they are legitimate.
To protect your cryptocurrency always get contract addresses from authentic sources and double check that the stats match the coin you are trading. For example if you wanted to buy Steve Wozniak’s new token $WOZX last month it would have been easy to create a token and fake the price, but it would be very hard to fake $50,000,000 in trading volume and a $1 Billion market cap.
Phishing scams can cast a large net like using a fake website to gather hundreds of people’s information and funds, or they can cast a single line to steal from a target they have isolated.
In 2014 a hacker gained access to the CEO of BTC media’s computer and used that access to trick the officers of Bit Pay into sending $1.8 million worth of Bitcoin to him. In this case the hacker didn’t even need to compromise his targets, he only needed to gain access to a trusted partner.
Fake ICOs
Scammers will go to great lengths to create a convincing project only to disappear on launch day. 2020 is the year of the rug pull.
Before investing your money be sure to engage in due diligence. Watch for red flags and investigate every aspect of a project.
- Read the whitepaper and road map
- Get to know the team and investigate their past
- Carefully consider the coin supply and tokenomics
- Consider the targeted use case and any alternatives
- Research the competition
- Inquire about contract and code audits performed by third parties
- Thoroughly understand the plan for the ICO or initial listings
- Check all popular communities and social networks for profiles and also comments from other people regarding the project
- A project either needs a reputable team with documented track record, publicly scrutinized smart contracts outlining liquidity or both
If your research leaves any room for doubt then you shouldn’t be investing.
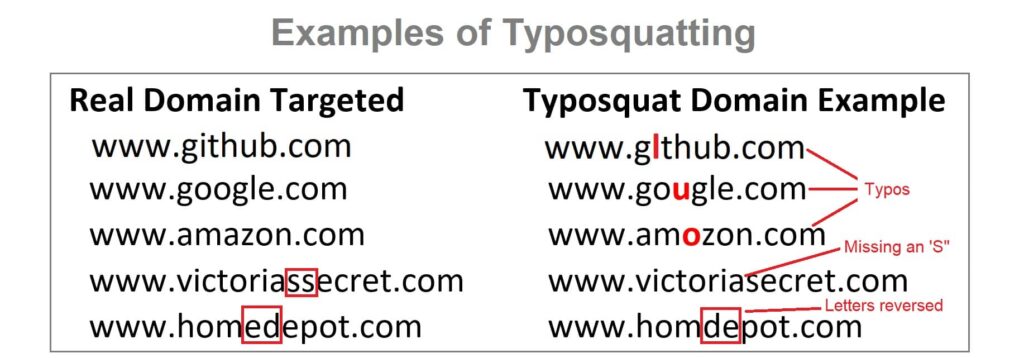
Fake Support Teams
The most prevalent scam is impersonation. Scammers will hang out in support channels and target new users asking for help. They will impersonate support staff and engineer a scheme to have you reveal your wallet’s seed phrase, give them access to your accounts or even send them cryptocurrency outright.
Assume that everyone is a scammer online and never give anyone access to your assets.
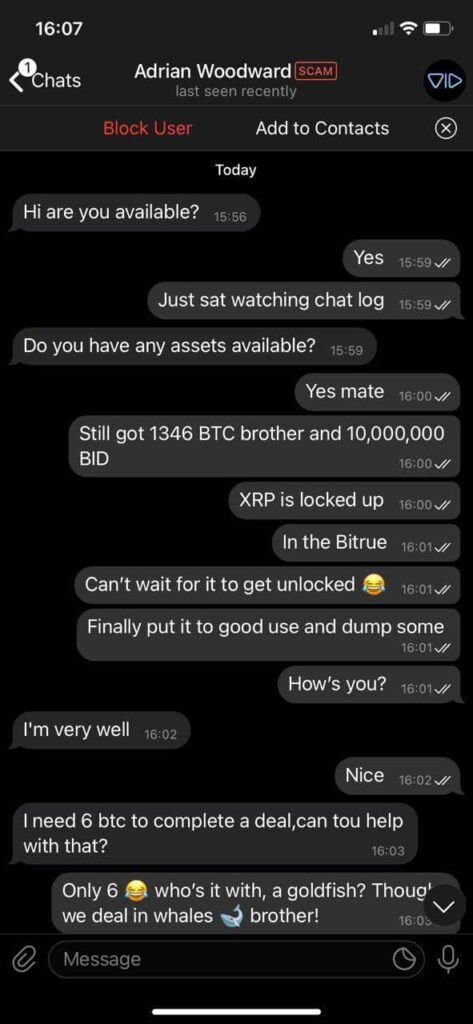
This is why administrators will often have “I will never DM first” or “I will never ask for money” in their names on Telegram.
Real product support will never ask you for passwords, ask to be sent money or ask you to reveal your key or seed phrase.
Fake Exchanges & Apps
Since many blockchain projects are open sourced some scammers will simply copy code from an existing project and create duplicate exchanges and software that have a back door built in to steal your funds.
Others will create entire websites or applications that report false gains but will not allow you to withdraw funds, or will only allow a very small amount to be withdrawn.
This is one reason governments are becoming more active with regulation. You should only sign up for legitimate well known exchanges and whenever possible move your assets to cold storage wallets you control the keys to.
This goes back to scrutinizing the apps and websites you use. It is your duty to protect your cryptocurrency by investigating everything you interact with.
Avoid Ponzi Schemes
If it sounds too good to be true, it probably is.
From 2015 to 2017 Ruja Ignatova managed to scam $4 Billion from unsuspecting investors all across the world with a dubious offering called One Coin that integrated a multi level marketing component.
These types of scams have become commonplace in the cryptocurrency market. The marriage of sophisticated con artists and a hungry public hoping for quick returns has been a fruitful one for the scammers, but not so much for the public.
Always investigate assets before you invest. Even legitimate companies will have detractors and there are scammers that specialize in planting fear and doubt for legitimate cryptocurrencies to create an opportunity to short sell the coins, but you should treat every accusation as a potential red flag until it can be debunked.
Don’t trust the research of others. Many people are repeating information they’ve heard somewhere else which could be traced back to someone who set a scam in motion.
When you begin investing in cryptocurrency it’s best to stick with high profile projects until you gain some experience. You will encounter hundreds of people trying to sell you the next big thing or a sure fire way of getting rich with little work or investment, but the best opportunities are the ones that everyone is already talking about.
Avoid any projects that:
- Promise returns that seem too good to be true
- Promise regular returns that are substantially higher than other investments
- Lack audits from reputable security experts
- Projects that aren’t proposing a solution to an existing problem – crypto for crypto’s sake
- Any project that doesn’t have crystal clear messaging and transparent goals
You’re Responsible for Protecting Your Cryptocurrency
I hope I’ve given you a good starting point for protecting your investment going forward. There are many other important facets to digital security and we will cover those in the coming weeks and months. Until then if you don’t know, ask someone before jumping in feet first.
It’s your job to protect your cryptocurrency. Try to keep it as simple as possible and consistently follow digital security best practices. As long as you follow the basics you will be a harder target than most and scammers prefer easy targets.
Always Be on Red Alert
Even if you do all of this correctly you are still at risk for targeted attacks. The only way to minimize those attacks is to understand the security features offered to you, continually monitor web activity and react with extreme measures every time you notice something strange.
For example hackers have been able to clone SIM cards. By intercepting your cellular communications they can reset your passwords without you even knowing.
In 2019 Sean Coonce learned about this sophisticated attack the hard way when hackers stole over $100,000 from his Coinbase account. Coinbase has published advice for protection against phone based attacks.
In most cases these targets are selected for their high value. This goes back to keeping a low profile online and using a dedicated email that no one knows for high value accounts.
To enjoy the highest level of security you should:
- Use a hardware or multi-sig wallet for your crypto. Only use on-ramps and exchanges when you are transacting.
- Secure your passwords with something more secure than mobile 2 factor authentication. Some options include Google Authenticator and YubiKey.
The problem is that most people move into Crypto with their existing security scheme that wasn’t designed for protecting your finances. Make no mistake that when you hold crypto you need to adopt a level of security on par with your bank’s digital security protocols.
I hope this article helps you protect your investments. Scammers and hackers only hurt the adoption of cryptocurrency so it is in all our best interests to fight against them.
This is not meant to be financial or security advice. Read our disclosures here.
- Bitcoin’s Lightning Network Explained - July 24, 2023
- What is Signature Aggregation? - October 5, 2022
- How John Hwang Built Rainier Arms and His Diverse Personal Investment Portfolio - February 22, 2021

